Chef 360 Platform access control
Chef 360 Platform employs a multi-layered access control model that integrates route-based access policies with Role-Based Access Control (RBAC).
Users or systems are assigned roles upon gaining access to an organization and each role is associated with a set of route-based access policies. When a request is made, the user must provide proof of identity and specify the role under which the request is made.
Certain service domains extend the RBAC model to include attribute-based access controls, object-level permissions, or Discretionary Access Control (DAC). For example, the Courier State service adds object-level permissions that restrict evidence upload only to the node that was assigned to the Courier job.
The access control strategy is harmonized across different services by applying the role to all requests in a single chain. The Application Programming Interface (API) gateway first evaluates the role to apply route-based rules, then the request is sent to a specific service that applies its own rules. If the service makes a call to another service, both the user’s identity and role are evaluated for route-based access, and the unique role assigned to that service is also validated. Chef 360 Platform only completes a request if both evaluations are true.
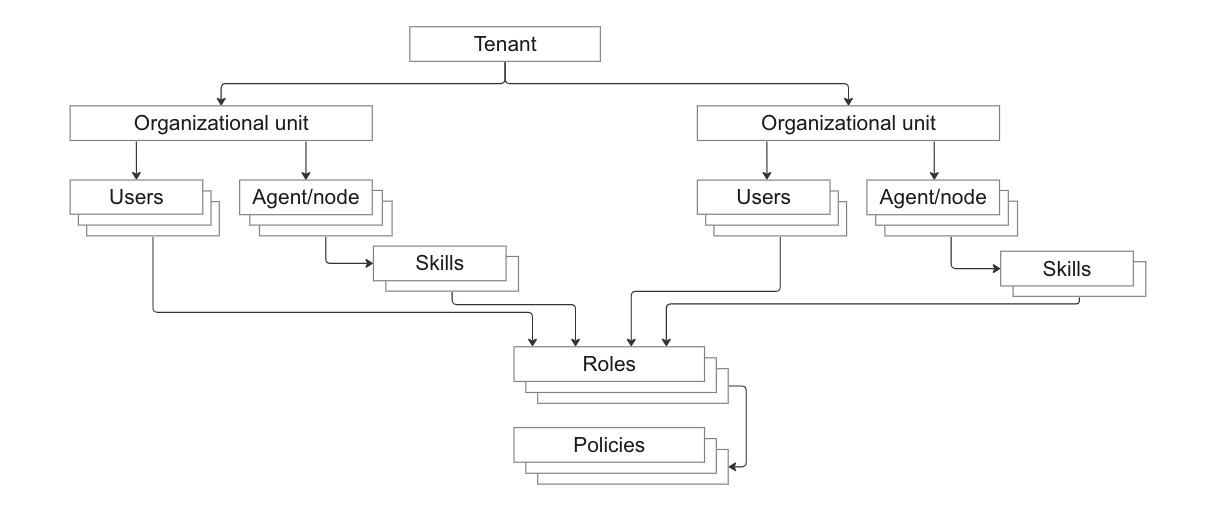
Role-based access control
Role-Based Access Control (RBAC) restricts system access to authorized users. This access control is based on the roles and privileges assigned to users, which determines their access rights within the system.
Chef 360 Platform RBAC enforces Separation of Duties (SoD) requirements, such as critical operations that require the involvement of two or more people.
Chef 360 Platform includes built-in roles. You can also create custom roles for an organizational unit to enforce any unique SoD requirements or specific Principle of Least Privilege (PoLP) rules. If needed, you can update these roles on every software release. These roles allow you to continuously evaluate the Principle of Least Privilege (PoLP) and reduce the roles to only have access to the intended services.
Route-based access policies
All access requests (internal and external) are subject to the application of route-based access policies.
Route-based access policies define rules for granting or denying access to resources based on the requested HTTP route/path and the role authorized for the HTTP request. The policy specifies conditions under which requests are allowed or denied based on attributes like the path, the requested action, and the accessed resource. For example, a policy might only allow users with the “Admin” role to create new users, while users with the “Viewer” role can only read data but not modify it. Policies are attached to roles and are evaluated at runtime to determine access rights.
Attribute-based access control
Attribute-Based Access Control (ABAC) authorizes operations by evaluating attributes of requested operations against the allowed set of operation policies, rules, and relationships.
Chef 360 Platform evaluates attribute-based access control rules at a service domain level after it evaluates the RBAC rules.
Discretionary access control
Discretionary Access Control (DAC) is a type of access control where the owner of a resource (like a node list or job template) has the authority to decide who can access it and what permissions they have. Users can be granted or denied access based on their identity or group membership, with permissions typically set for actions like read, write, and execute. DAC provides flexibility in managing access rights, allowing owners to tailor permissions to individual user needs.
Object-level permissions
Object-level permissions are access controls applied directly to specific objects within a service (such as jobs and nodes). These permissions determine what actions individual users or groups can perform on each object, such as read, write, delete, or modify. Object-level permissions provide granular control over access, allowing for precise security management within an application or database.